It is a process of protecting APIs from malicious attacks or misuse. Unfortunately APIs are becoming a primary target for attackers. To secure API, it includes API access control and privacy, as well as the detection and remediation of attacks on APIs through API reverse engineering.
API Security Works like
Authentication: Checks the identity of an end-user. All the application malfunctioning attempts are blocked at the application level
Authorization: Determines the resources an identified user can access
Another layer of security: An extra layer of security is created between the client and data, by throttling sensitive information in the API response
Best Practices to secure API
Inventorying API
API Access Control
Threat Detection API Security
Testing Monitoring and Analytics Across API data
Continuous Auditing and Incident Response
Advantages with API Security
Encrypt traffic/data using TLS
Don’t expose more data than necessary
Strong authentication and authorization solutions are used
Prioritize security
Inventory and manage your APIs
Practice the principle of least privilege
Remove information that’s not meant to be shared
Validate input
How can we secure our API?
Encrypting data through TLS (Transport Layer Security)
Access Control
Throttling sensitive information in the API communication
Remove unnecessary information
Hashing passwords
Validating data
Securing API by establishing an HTTP connection
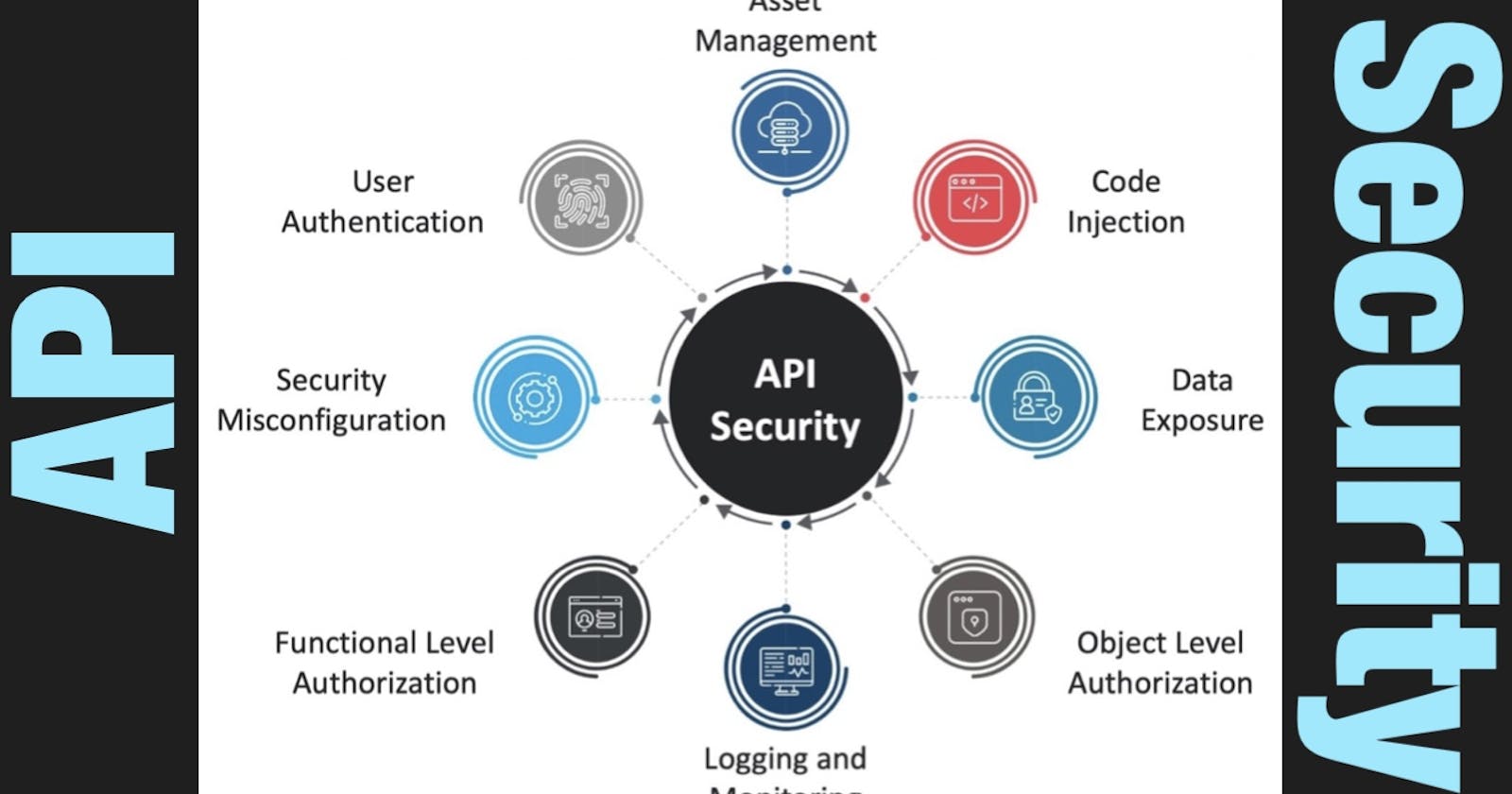
To secure API, it is important to check vulnerabilities like user authentication, object and function level authorization, code injection, lack of rate limiting, security misconfiguration, and asset management. Nowadays, DevSecOps team must test APIs to identify vulnerabilities and address these vulnerabilities using best security practices regularly!
Compiled by: Azizul maqsud
LinkedIn: https://www.linkedin.com/in/azizul-maqsud/
Reference : https://lnkd.in/dQ67Y279