Why the 7 Layers Security becomes a MUST for Cybersecurity / DevSecOps Models?
Especially for a small or Medium Sized Business (SMB), it is required...
7 Layer security becomes Crucial for Cybersecurity / DevSecOps Models nowadays. Especially for a small- or medium-sized business (SMB), it is required to be aware of the potential risks and vulnerabilities that come with running a modern business. In spite of having some regulatory security measures, it is now mandatory to understand that there are 7 crucial facets / Layers of IT security that you need to consider to fully secure your SMB.
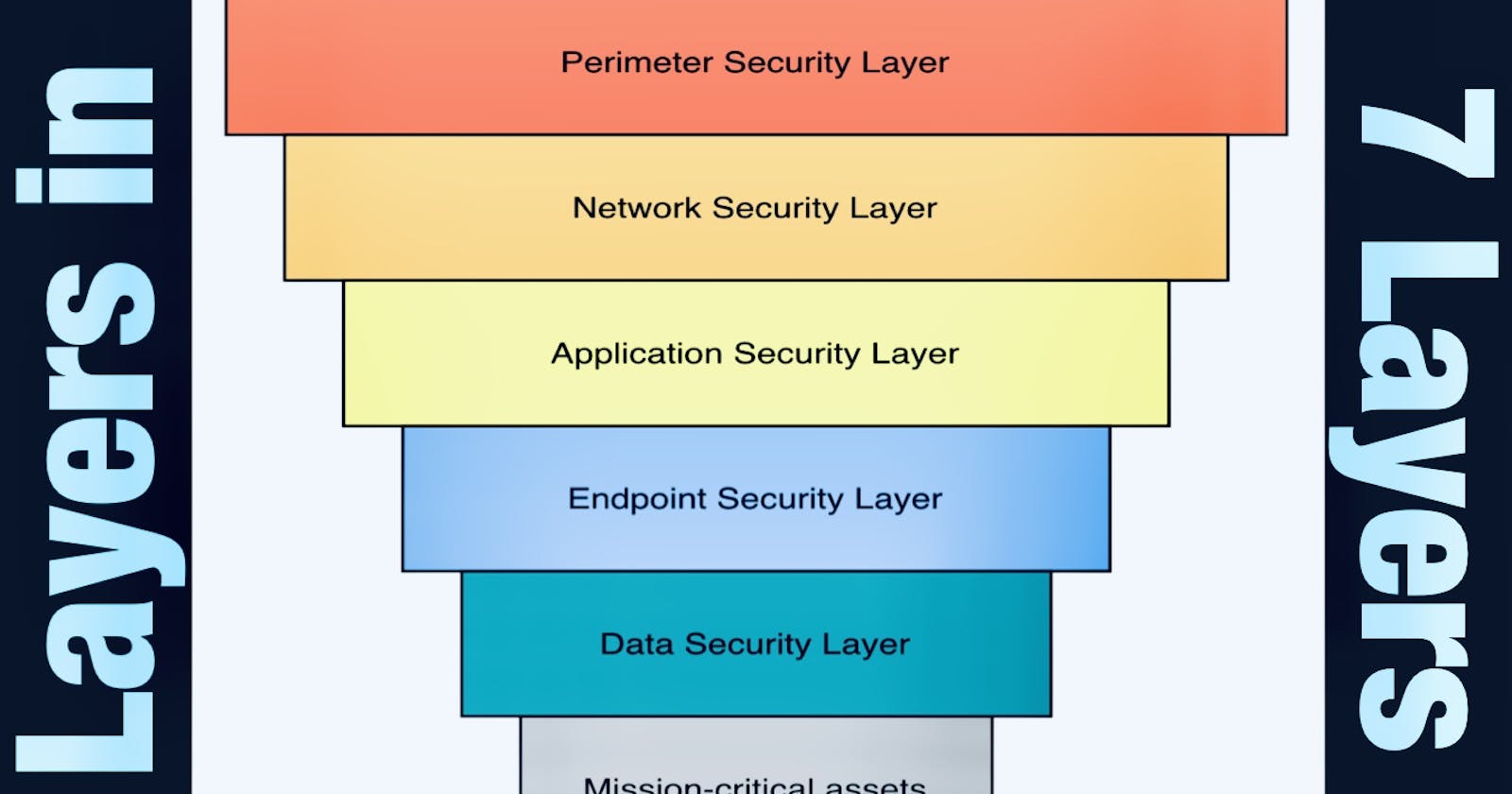
Physical security / Human Layer
People who have access to your network, whether they are employees, contractors, or customers. It’s important to have security measures in place that will educate and train users on how to identify and avoid potential threats like phishing awareness training, multifactor authentication, and password management.
Perimeter Security/ Perimeter Layer
This is the layer of the network that separates it from the rest of the internet. It comprises devices that control traffic flows in and out of the network, including firewalls, routers, and switches.
It implements a robust firewall policy to block unwanted traffic and prevent malware and other threats from entering your network.
Network Security / Network Layer
This layer comprises the people as well as the devices that have access to your servers, computers, mobile devices, and other network-connected devices such as printers and scanners. The most effective way to secure this layer is by implementing the principle of least privilege or permissions to access. This reduces the risk of data breaches and insider threats.
Endpoint Security / END-POINT Layer
The number of devices that are connected to your network is a potential entry point for hackers. Using antivirus, anti-malware, and access control software at the endpoint level is a must to secure endpoint devices. You can use mobile device management software to remotely control and manage the settings and security of all the devices that are connected to your network. Mobile devices also enable you to remotely wipe data from lost or stolen devices, effectively preventing sensitive information from falling into the wrong hands.
Application Security / Application Layer
Applications like your email server, web server, and file-sharing apps, are at risk also. Ot is required to make sure that all the applications running on your network are up to date and patched. You can implement application whitelisting, a mechanism that allows only approved apps to run on your network.
Data Security/ Data Layer
Encryption is the most effective method for securing data, as it makes data unreadable to anyone who doesn’t have the encryption key. Also, it should be implemented a data loss prevention solution, which helps to detect and prevent sensitive data from being leaked.
MISSION-CRITICAL Assets Layer
It refers to anything in business that can’t function without critical applications, servers, databases, and more. It varies from business to business, so it’s important to assess your SMB’s most vital technologies and information.
You should also consider implementing redundancy such as having backup servers or applications, to ensure that your business can continue to operate even if mission-critical assets are compromised.
In conclusion, we can reiterate the OSI model which was invented in the late 1970s comprising seven layers. Now, these layers are the different aspects to secure and protect your IT infrastructure and business data. And, for DevSecOps, nowadays, these seven crucial layers of IT security become a MUST to secure your network, data, and business.
Compiled by: Azizul Maqsud
References:
https://www.outsourceitcorp.com/the-7-crucial-layers-of-it-security/
https://www.educative.io/answers/what-are-the-seven-layers-of-cyber-security
Stay Connected !!
https://www.youtube.com/channel/UCNwP7KEElaJ7cdDTLP-KbBg
https://www.linkedin.com/in/azizul-maqsud/
https://azizulmaqsud-1684501031000.hashnode.dev/