Table of contents
No headings in the article.
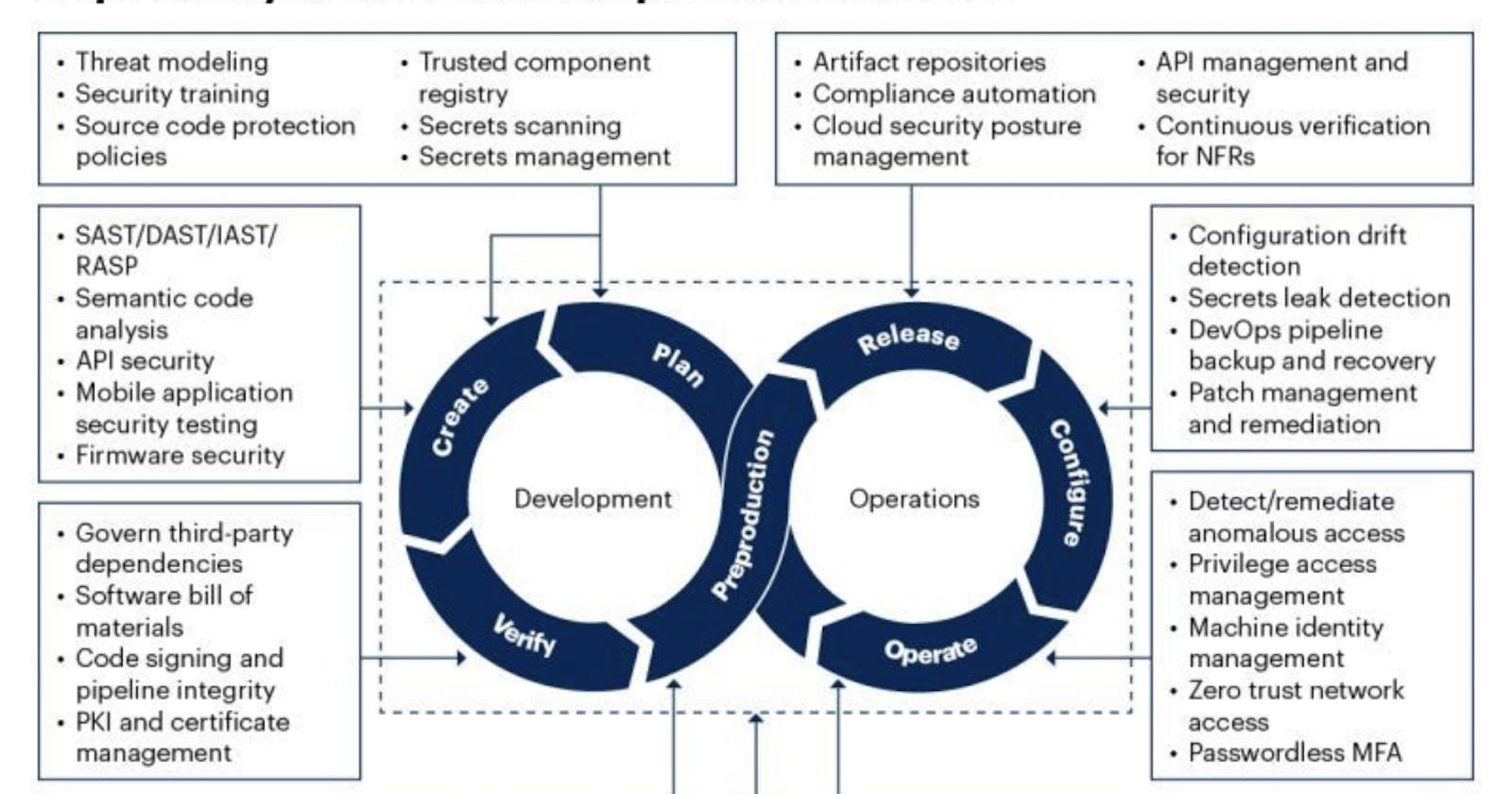
Implementing DevSecOps in SDLC is a journey to involve a continuous security best practices and tools. It's not just about the tools, but also the processes practiced by the team in discipline!
Pinpoints:
Identify security requirements: Identify and document the security requirements for the application or system that is being developed. This includes identifying potential threats and vulnerabilities. Implement IAM Best Practices. Implement the least privilege access, i.e., give only the required access to individuals. Use IAM tools to manage access to resources effectively.
Threat: Leverage threat intelligence tools to stay ahead of potential threats and vulnerabilities.
Responsibility: Make Security a Shared Responsibility. This is the primary tenet of DevSecOps. All members of an organization are responsible for security in DevSecOps, not just the security team. Developers need to write secure code, QA teams need to test security aspects, and operations teams need to ensure secure deployments.
Hardcode: Never hardcode secrets or sensitive information in your code or configuration files. Use secrets management tools for this purpose.
Integration into the SDLC: Incorporate security into the software development life cycle (SDLC) by integrating security testing and other security practices into the development process. Integrate Security from the Start. Do not leave security as an afterthought. Integrate security practices right from the planning and design phase. The tools for SAST and SCA can be used from the early stages to ensure that the code written is secure and that the third-party components used are not vulnerable.
Use of automation: Use automated tools and processes to integrate security into the SDLC. This includes using tools such as static code analysis, dynamic analysis, and penetration testing. Automate Wherever Possible. DevSecOps relies heavily on automation. Use CI/CD pipelines to integrate and deploy code automatically. Automate the execution of SAST, DAST, IaC security, and container security checks as part of the pipeline. Automate compliance checks as well. The aim is to identify and fix security issues as early as possible.
Continuous monitoring: Implement continuous monitoring to detect and respond to security breaches in real-time. This includes using tools such as intrusion detection and prevention systems and security information and event management (SIEM) systems.
Collaboration: Encourage collaboration between development, operations, and security teams to ensure that security is integrated throughout the SDLC.
Security training: Provide training to developers and other team members on secure coding practices and other security-related topics. Regular Training and Awareness. Conduct regular training sessions for all the organization's members to keep them updated on the latest security threats and best practices.
Compliance: Ensure that the application or system being developed complies with relevant security regulations and standards.
Response: Respond Quickly to Incidents. Security incidents might happen despite all precautions. Have an incident response plan in place. This should detail the steps to be taken in case of a security incident.
Continual improvement: Continuously monitor, assess, and improve the security of the application or system throughout its lifecycle. Implement continuous monitoring practices to detect any security threats or issues in real-time. Use SIEM tools for this purpose. Also, ensure proper logging of all events for future reference.
Audits: Frequent audit your security practices and tools. Ensure all the tools are up-to-date and all the security practices are correctly followed.
Compiled by: Azizul maqsud
Reference:
https://www.devsecopsnow.com/how-to-map-security-needs-to-devsecops-tools-in-sdlc/